Showing posts with label Technology News. Show all posts
Showing posts with label Technology News. Show all posts
Google Refused to Remove MP3 Download Technology
Google has refused requests to remove MP3 Music Download Pro, an extremely popular Android Technology app which allows users to download copyrighted music onto their phones, according to the RIAA.The app, which PC-Mag.com highlighted this technology.
Thursday, is now the fifth most popular free app on the Android Market, jumping past Google Books in a single day. Other free apps on the Market, such as Easy MP3 Downloader and MP3 Music Download Super technology, also advertise the ability to "search and download free music & lyrics from other forums.We sent a take down notice to Google in August for this particular technology, which is clearly being used for illegal purposes, and Google responded that they were declining to remove it from the Android Market," the RIAA spokeswoman said. "We continue to have concerns with Google's screening and take down procedures and hope that they will be improved technology.
It's unclear, however, whether all consumers would choose to purchase licensed music via Google's store, when they could freely (but illegally) download it via the MP3 downloader apps technology that Google has published on the Market. Representatives at Universal Music, Warner Music, and Sony Music did not return calls seeking comment.
PCMag.com also requested a comment from Google on Thursday and again on Friday on MP3 Music Download Pro and related apps technology. Although a Google spokeswoman acknowledged to receiving the request on Thursday, the company has not yet responded.
Industry sources indicated, however, that Google declined to take down the MP3 Music Download Pro app technology because the search giant apparently felt that the app could be used for legitimate purposes. Screenshots posted by the developer Yu Liu had shown the app being used to search for classical music, which may or may not be in the public domain, depending on the performer. On Friday, that screenshot with the search results was not there.
Android Technology mp3 downloads
New Technology 'Server on a Chip' Aims to Lighten Up Cloud Hardware
Servers don't just cost money also cost technology space and power. In order to address those issues, a company called Calxeda is developing Energy Core technology, a so-called server on a chip. It's taking notes from a sector in which space conservation and the optimization of power consumption are top priorities: the cellphone industry.
While the image that the high-tech industry has adopted for the source of services delivered over a remote network -- the cloud technology -- conjures thoughts of airy skies where quasi-magical things happen, the actual cloud is firmly anchored to the ground in data centers bristling with computer servers. As the cloud continues to expand, so does the demand for servers technology -- servers that consume more and more resources like electricity, space and capital.
An obvious answer is to create servers technology that consume less power, take up less space and cost less to deploy. And that's what a company called Calxeda says its new EnergyCore "server on a chip" will do for servers that use it.Calxeda announced its EnergyCore processor Tuesday at simultaneous events held in Austin, Texas, where the company is headquartered, and Palo Alto, Calif., where HP (NYSE: HPQ) revealed its intention to include the chip in its first generation of extreme low-energy server technology development platforms.Tech News World
"Most large enterprises, and even Web-scale companies, have an insatiable need for more power in the data center," Calxeda Director of Product Marketing John Mao told TechNewsWorld, "and the top constraining factors that they face to obtain that power is the lack of energy running into the buildings and the amount of space that they have."Data center operators will tell you that they have plenty of money and budget to buy more servers, but they can't get them physically deployed because of those two reasons," he added.A problem with a server based on ARM technology is that it doesn't support 64-bit processing, according to SeaMicro CEO Andrew Feldman. Because ARM only supports 32-bit processing, it can't address as much memory as a 64-bit processor technology, he explained.
"Each core gets only one gigabyte of memory," he told TechNewsWorld. "That's very little memory."
Calxeda's Mao, however, discounted the need for a 64-bit processor technology. The reason nearly all data centers use servers with 64-bit processor is that they can't get their hands on servers with 32-bit processors, he opined. "There have been a lot of end-users that have come back to us and said, 'You know what? Actually, 32-bit will work.'"
technology used
However, "it won't work for everything," he conceded. "But where it matters for efficiency, 32 bits is just fine. In fact, it may be better because it's more efficient than what they've seen on their other platforms."Peter ffoulkes, research director for servers and virtualizaton technology for the 451 Group in Boston, also frowned on the importance of 64-bit support."It's not that big of an obstacle," he told TechNewsWorld. "There's an awful lot of people still running 32-bit applications."Moreover, the kind of jobs the processors would be called on to do could easily be distributed across a number of 32-bit processors just as well as a number of 64-bit ones, he explained."You don't need a big 64-bit memory space to do that," he said. "You just give each processor two gigs of data or four gigs of data at a time and let them work on it."For companies with thousands of servers delivering Web services, social media and simple content delivery applications, HP said, Project Moonshot is designed to deliver new and improved technology simplicity while achieving energy and cost savings never before possible.
Google's New Algorithm Technology For Publishers
Peoples who live and die according to how well they can suss out Google's search algorithms to drive traffic technology, the company's constant tinkering may create a giant headache. The best "trick" may be to ignore the algorithms and focus on providing quality content, suggested Melanie Rembrandt of Rembrandt Communications. "Those who provide valuable content to their target market will always be rewarded.Google is introducing a change to its search algorithm technology that will impact some 35 percent of searches on the Internet. The end goal of the massive shift is to encourage publishers to keep content as fresh as possible, especially as it relates to recent news and events technology that are regularly updated.For example, "If I search for [olympics], I probably want information about next summer's upcoming Olympics, not the 1900 Summer Olympics," wrote Google fellow Amit Singhal in a blog post."Google Search uses a freshness algorithm technology, designed to give you the most up-to-date results, so even when I just type without specifying 2012, I still find what I'm looking for.....
The so-called freshness algorithm technology is good news at first glance, but it comes with a downside for retailers and SEO marketers -- and possibly for consumers too.
The changes might encourage publishers to constantly update content to the point where the value-add is meaningless, all in the name of staying on top of the search rankings, Gabe Donning, lead analyst at Chitika, told TechNewsWorld technology."There definitely is the potential to increase spam and decrease relevancy,
" he said.
For marketers, the change means coming to grips with yet another in a long string of Google algorithm adjustments. Google has been tinkering with its Panda algorithm, which it launched earlier this year to weed out content farms. It also began encrypting searches and outbound clicks technology.Even positive changes require some work in order to adapt to them, and Google's freshness algorithm update will require a significant amount of rethinking on the part of publishers.
Google's goal is clear -- make users happy -- and in 2011, the only way to do that is to provide the best results that are most relevant and timely for users," William Toll, vice president of marketing at Yottaa, told TechNewsWorld......It can be easy to get carried away by all of the SEO updates technology, changes and trends out there," Rembrandt continued, "but if you give your customers valuable content while using the appropriate SEO keywords and coding , you can bring in new customers, offer interesting information to current customers, and please the search engines too.
Adidas shuts down sites after cyber attack
On November 3, 2011, the adidas Group found out that it was the target of a sophisticated, criminal cyber-attack. Our preliminary investigation has found no evidence that any consumer data is impacted," the company said in a statement on its news stream site. "But, while we continue our thorough forensic review, we have taken down affected sites, including Adidas.com, Reebok.com, mi Coach.com, Adidas-group.com and various local eCommerce shops, in order to protect visitors to our sites.
The company has put in place additional security measures, the statement added, without going into details. The company also did not say what happenedAs of this afternoon, Adidas.com and mi Coach.com were still inaccessible. "Due to technical difficulties our website is currently not available," the Adidas site said.
"We are working to restore the site as soon as possible. As the site was also scheduled for a number of exciting updates, we will use the current down time to make those changes," the mi Coach.com site said. "This way the site will launch again with the latest and greatest developments already in place."
The message on the mi Coach site said the company was aiming to have the site back up by the end of day on Tuesday.
Panasonic reveals industrial-strength Android tabletsThe company announced yesterday that it plans to sell two models of rugged Android tablets under the Toughpad brand name starting in 2012. The 10-inch, $1,299 Toughpad A1 will arrive first, in the spring.Panasonic isn't aiming the Toughpads at the average consumer, but rather to various business users such as utility crews on the road, military staff in combat situations, or doctors making their rounds. It's a tablet extension of the approach the company already takes with its Tough book line of rugged PCs.
But I still see the products as good news for average consumers as durability becomes a selling point. Gorilla Glass has meant that buyers of higher-end smartphones don't have to worry about screens scratched by keys and coins, and an ever-broader array of cameras and video cameras are shockproof and waterproof. Durability adds complexity and expense to a device, but it's a feature that I think customers will appreciate and and pay for at least in moderate doses. Among the Toughbook A1's mainstream specs: a 1.2GHz dual-core processor; Android 3.2 aka Honeycomb; a "daylight-readable," LED-backlit, 1024x768 touchscreen display; 1GB of DDR2 memory; options for WiMax or LTE 4G wireless networking or more conventional 3G newtorking; a front-facing 2-megapixel camera and rear-facing 5-megapixel camera with an LED flash; ports for micro USB, micro SDHC, and HDMI; and a 33.9 watt-hour lithium-ion battery. It measures 10.5x8.3x0.67 inches and weighs 2.1 pounds.
With a price that's hundreds of dollars more than a conventional tablet, mainstream customers won't pay for the Toughpad. I wouldn't be surprised also if its daylight-readable, anti-glare screen doesn't look as good for those who mostly play games or videos indoors. The novel specs come later, though: operating temperatures between 14 degrees and 122 degrees Fahrenheit, drop-test rating to 4 feet, a magnesium alloy chassis with elastomer bumpers on the corners, hardware security features, the ability to withstand thermal shocks from rapid changes in temperature, a protected screen, port covers to keep out dust, vibration resistance, a field-replaceable battery, and compliance with the MIL-STD-810G military standard for environmental engineering. It's also got a stylus, a good feature for precision input.
Inside Facebook's massive cyber-security system
FACEBOOK has released details of the extraordinary security infrastructure it uses to fight off spam and other cyber-scams.Known as the Facebook Immune System (FIS), the massive defence network appears to be successful: numbers released by the company this week show that less than 1 per cent of users experience spam. Yet it's not perfect. Researchers have built a novel attack that evaded the cyber-defences and extracted private material from real users' Facebook accounts.
t protects against scams by harnessing artificially intelligent software to detect suspicious patterns of behaviour. The system is overseen by a team of 30 people, but it can learn in real time and is able to take action without checking with a human supervisor.But inside Facebook's network it's much more persuasive. "It's easier to exploit trust relationships in online social networks," says Justin Ma, a computer scientist at the University of California, Berkeley, who develops methods to combat email spam.
Facebook's privacy settings allow users to shield personal information from public view. But because the socialbots posed as friends, they were able to extract some 46,500 email addresses and 14,500 physical addresses from users' profiles– information that could be used to launch phishing attacks or aid in identity theft.A socialbot attack is yet to happen, but it's only a matter of time. Socialbots behave differently to humans that enter Facebook for the first time, in part because they have no real-world friends to connect with, and their random requests lead to an unusually high number of rejections. FIS would be able to use this pattern to recognise and block an attack of socialbots, says Stein. That would put Facebook back on top– if only until hackers release their next innovation.
American Drone Technology
How does the American drone or unmanned aerial vehicle (UAV) work and determine its target? Al Qaeda had found the way the drone does its job.
The American and Pakistani intelligence stated that the American unmanned aerial vehicles (drone) are very successful in eliminating the Mujahideen in Pakistan. Those drones had launched 28 attacks on the suspected Mujahideen so far for this year. Thousands of innocent civilians had been martyred as a result of the drone attacks.
But how does the drone work and find its targets? Mullah Nazir, one of the local commanders of the Taliban in Pakistan had discovered it.
"Those aircrafts are guided by a SIM card which was usually inserted into a cell phone and used by the Mujahideen, through the enemies’ spies that had managed to infiltrate and be amongst the Mujahids," he said. The SIM Card sends a signal to the satellite which will guide and tell the drone to shoot its missile.
All these were explained in the book, The Ruling Concerning Muslims Spies authored by Abu Yahya al-Libi, one of the leaders of Al Qaeda. The book can be accessed directly for free on the internet.
The pictures of the SIM Card which can sufficiently use a 9 volt battery were also displayed in the book. The Chips send signals which are strong enough. The gadgets were made by Cejay Engineering, used by the American military and its allies to determine the position of their opponents, identify the location for the missile’s dropping point and also to map the defence lines.
The gadgets use a special LED with a 9 volt battery in order to send signals and the beams coming out from the LED could not be seen by the naked eyes. However, a Night Vision tools might be used, similar to the way the infrared works where the beam could not be seen directly by the naked eyes. The beams from the LED could be seen by using a special gadget from a distance of five miles. In fact, the beam could even penetrate the clothes and could still be seen under water.
The 9 volts battery could withstand up to 100 hours. Actually, a technology of this kind had already been around since 1984, however, most of them were only used for the military purposes. Both of the American Predator Aircraft and unmanned aerial vehicle are equipped with infrared cameras to receive the signals sent by the SIM Card mentioned earlier, almost similar to the way the normal remote control for the TV works, though with a more sophisticated technology as they are used for the military purposes.
However, those gadgets could now be purchased online and it only costs 25 dollars for each piece of the Chipset. The gadgets could be given to the spies or informers, and they would not cause any suspicion in the beginning, only that the spies have to place them somewhere and the American Drone would then respond.
Last April, Habibur Rehman from Pakistan made a statement of confession that he was a spy and worked for the enemies to place the chip before he was executed by the Taliban fighters thereafter.
"I was given a 122 dollars amount of money to wrap the chip with a piece of cigarette paper and then plant it at the house of a Taliban or Al Qaeda fighter," he said. “If I succeed, I was told that I’d be given thousands of dollars more,” Habibur Rehman said before he was executed.
Rehman also said that he did not only place the chips in the territories of the fighters, but also in other areas where there were lots of civilians to the extent that it had caused hundreds of people killed because of his actions as a spy.
"I knew that I could cause death to the people because of my actions, but I really need the money," he added.
The Taliban are really not joking in dealing with the spies, soon as they are captured, there is no choice but to execute them.
How does the American drone or unmanned aerial vehicle (UAV) work and determine its target? Al Qaeda had found the way the drone does its job.
The American and Pakistani intelligence stated that the American unmanned aerial vehicles (drone) are very successful in eliminating the Mujahideen in Pakistan. Those drones had launched 28 attacks on the suspected Mujahideen so far for this year. Thousands of innocent civilians had been martyred as a result of the drone attacks.
But how does the drone work and find its targets? Mullah Nazir, one of the local commanders of the Taliban in Pakistan had discovered it.
"Those aircrafts are guided by a SIM card which was usually inserted into a cell phone and used by the Mujahideen, through the enemies’ spies that had managed to infiltrate and be amongst the Mujahids," he said. The SIM Card sends a signal to the satellite which will guide and tell the drone to shoot its missile.
All these were explained in the book, The Ruling Concerning Muslims Spies authored by Abu Yahya al-Libi, one of the leaders of Al Qaeda. The book can be accessed directly for free on the internet.
The pictures of the SIM Card which can sufficiently use a 9 volt battery were also displayed in the book. The Chips send signals which are strong enough. The gadgets were made by Cejay Engineering, used by the American military and its allies to determine the position of their opponents, identify the location for the missile’s dropping point and also to map the defence lines.
The gadgets use a special LED with a 9 volt battery in order to send signals and the beams coming out from the LED could not be seen by the naked eyes. However, a Night Vision tools might be used, similar to the way the infrared works where the beam could not be seen directly by the naked eyes. The beams from the LED could be seen by using a special gadget from a distance of five miles. In fact, the beam could even penetrate the clothes and could still be seen under water.
The 9 volts battery could withstand up to 100 hours. Actually, a technology of this kind had already been around since 1984, however, most of them were only used for the military purposes. Both of the American Predator Aircraft and unmanned aerial vehicle are equipped with infrared cameras to receive the signals sent by the SIM Card mentioned earlier, almost similar to the way the normal remote control for the TV works, though with a more sophisticated technology as they are used for the military purposes.
However, those gadgets could now be purchased online and it only costs 25 dollars for each piece of the Chipset. The gadgets could be given to the spies or informers, and they would not cause any suspicion in the beginning, only that the spies have to place them somewhere and the American Drone would then respond.
Last April, Habibur Rehman from Pakistan made a statement of confession that he was a spy and worked for the enemies to place the chip before he was executed by the Taliban fighters thereafter.
"I was given a 122 dollars amount of money to wrap the chip with a piece of cigarette paper and then plant it at the house of a Taliban or Al Qaeda fighter," he said. “If I succeed, I was told that I’d be given thousands of dollars more,” Habibur Rehman said before he was executed.
Rehman also said that he did not only place the chips in the territories of the fighters, but also in other areas where there were lots of civilians to the extent that it had caused hundreds of people killed because of his actions as a spy.
"I knew that I could cause death to the people because of my actions, but I really need the money," he added.
The Taliban are really not joking in dealing with the spies, soon as they are captured, there is no choice but to execute them.
Hackers Threaten to Take Down Facebook
Hacker group that claims to be Anonymous posted a YouTube video proclaiming it planned to attack Facebook on November 5. The video has since been removed, but analysts believe the video could be a scare tactic being used by the group, or even the work of an imposter.Facebook is a likely target for Anonymous because the social network has often been at the center of privacy concerns regarding its user's information.Everything you do on Facebook stays on Facebook, regardless of your privacy settings, and deleting your account is impossible," said a decoded voice in the YouTube video. "Changing the privacy settings to make your Facebook account more private is a delusion. Facebook knows more about you than your family."
The official websites and Twitter accounts of Anonymous have not confirmed the attack, making it a distinct possibility the plan is a hoax. However, the reaction the threat has garnered speaks to the growing prevalence of hackers, especially politically motivated groups with an agenda to advance, particular when it concerns free speech and privacy.
Hacktivist groups like Anonymous and LulzSec have proven over the past year they have the resources and might to threaten large corporate and government systems. The initial hacks of Sony's PlayStation Network were reportedly the work of Anonymous and LulzSec, and the two groups have also been blamed for the breaching of several government websites.
Anonymous also lead the charge against San Francisco's BART transit system, which shut down mobile connectivity during protests earlier this year.
Most recently, Anonymous scheduled and later called off an attack against Mexico's Zetas drug cartel for murdering online dissenters. The group called off the attack after the cartel began hiring their own hackers to hunt down Anonymous members.Despite the failure of the attack on the drug cartel, Anonymous' announcement that it planned to target the group invited a real fear that it would happen. The same is true for the Facebook hacks, and the group may have the abilities to make a shutdown on the powerful social network happen.
Evaluation Era Of Computer Programming Languages
Visual C++, Java, Javascript and PHP. I remember me and a couple of my friends in the same program also had to take a class in Assembly language together with the Computer Engineering students. Boy, was that an ordeal! We were just glad to be able to pass that subject. Hehe
For me the most interesting computer language to learn is PHP but unfortunately, we only had a short period of time to learn it. Anyways, talking about computer languages or programming languages, let us go back down memory lane with an info graphic created by the folks of Backspace about the Evolution of Computer Languages. There are hundreds of computer languages or programming languages but this info graphic features the ones that are the most popular and widely.
From the Backspace blog:
Visual C++, Java, Javascript and PHP. I remember me and a couple of my friends in the same program also had to take a class in Assembly language together with the Computer Engineering students. Boy, was that an ordeal! We were just glad to be able to pass that subject. Hehe
For me the most interesting computer language to learn is PHP but unfortunately, we only had a short period of time to learn it. Anyways, talking about computer languages or programming languages, let us go back down memory lane with an info graphic created by the folks of Backspace about the Evolution of Computer Languages. There are hundreds of computer languages or programming languages but this info graphic features the ones that are the most popular and widely.
From the Backspace blog:
All the cloud applications you use on the Internet today are written in a specific computer language. What you see as a nice icon on the front end looks like a bunch of code on the back end. It’s interesting to see where computer languages started and how they have evolved over time. There are now a series of computer languages to choose from and billions lines of code. Check out the info graphic below to see the computer language timeline and read some fun facts about code along the way.which is the best language with respect to all aspects of programming language???
Apple reportedly fires employee for negative Facebook post
While there are those who believe social media is opening the gilded doors to a new world of joyous connection, some might wonder whether there's a slight downside for those who are able to make that joyous connection.Apple reportedly has strict rules about posting any negative comments on any social media sites in order to protect its commercial reputation. So the company fired Crisp for gross misconduct, according to the report.
The UK labor tribunal upheld this right because it declared that posting even on your own private Facebook page doesn't give privacy protection. Any one of your friends could copy and paste those comments and effectively publish them..
This is what reportedly happened here. A Facebook friend showed the comments to the Apple store manager and Crisp was burned.
This isn't the first time, naturally, that someone in retail has been fired because of something uttered on Facebook. Last year, for example, a server in a North Carolina restaurant was fired for expressing that she thought the customers cheap.
However, this decision raises a troubling precedent. If the court believes that the mere potential for copying and pasting negates an individual's right to privacy, then even personal e-mails sent, say, to a former lover and her mother might also be deemed not private.
The court here relied on the fact that Apple's image is very important to its commercial success. So imagine if an Apple store employee wrote to her lover's whole family: "My iPhone 4S battery sucks more than the Indianapolis Colts."
Imagine, then, that she falls out with her lover and he still has the e-mail. What if he shows it to her employer?
While e-mail isn't classified as a social network, might some enterprising lawyer attempt to show that sending an e-mail to more than one person--or even just to one--makes that message social by definition?
Twitter spotlights tweets
Normally an avenue for broadcasting news, opinions, and users' locations, Twitter is now highlighting the inspirational ways single tweets have had a positive impact on users' lives.
Tales at a new site called Twitter Stories range from movie critic Roger Ebert's use of the service after he lost his voice, to a man who found a kidney donor after tweeting "Sh*t, I need a kidney," to a man who saved his mother's bookstore with a tweet, to pro football player Chad Ochocinco treating 100 followers to dinner with a surprise invitation delivered across the service.WikiLeaks' Assange to be extradited
WikiLeaks editor Julian Assange has lost his bid to avoid extradition to Sweden to face questioning over allegations of sexual assault.On Wednesday, the High Court in London said the 40-year-old Australian must comply with an extradition ruling made by chief magistrate Howard Riddle in February. Assange has been living in the U.K. under bail while his appeal was heard.
Assange's lawyers argued that the WikiLeaks editor would not be able to get a fair hearing in Sweden and that the Swedish prosecutor making the extradition request is not qualified to issue the European Arrest Warrant served on Assange.
Some of Assange's backers have suggested the U.S. has exerted influence on Sweden to push on with the extradition and questioning. WikiLeaks embarrassed the U.S. when it published thousands of thousands.
Flying car in mid-2015
A flying car in mid-2015? There are no guarantees in the world of envelope-pushing, mind-bending military techknown more casually as the “flying Humvee” initiative. Both designs have moved to Phase 2, which requires them to begin work on prototypes for evaluation at the end of fiscal 2012.This development also brings us a full phase closer to Phase 3, which is where things get really interesting: ground and flight demonstrations, slated for mid-fiscal 2015 should Phase 2 come off as planned.
That’s just four years from right now. Given that we’ve been waiting for our cars to take flighYou may recall from our relentless fawning over the Transformer program that the flying Humvee needn’t just be a roadable aircraft. Its design parameters call for a durable on- and off-road capable vehicle that can take small arms fire in stride and make a speedy shift from ground vehicle to vertical-takeoff-and-landing aircraft. It also needs to be easy enough to pilot that any grunt with a driver’s license can also grab the sticks of this new flying machine and be expected to pilot it safely (presumably with the help of autonomous computerized flight controls).
So you’re looking at some design incongruities there. It needs to be light enough to lift off vertically under its own power, yet will require a serious power plant (weight) and some kind of wings and/or propeller/ducted fan (more weight). It also needs space for all this extra hardware while still maintaining passenger space for four soldiers (including driver).
Like most of DARPA’s challenges, bringing this one to life won’t be simple. But speaking to a conference recently, DARPA Transformer program manager Stephen Waller told attendees that “we are seeing feasible designs,” Aviation Week’s Ares blog reports. That’s promising. Let’s just hope these things can actually get off the ground.
Pakistan to launch satellite in 2011
SLAMABAD -Pakistan will launch its first indigenously developed communications satellite on August 14, 2011, from a facility in China and the satellite's life span will be 15 years.
According to sources in Space and Upper Atmosphere Research Commission (SUPARCO), the satellite would be launched at a longitude of 38 degrees in geostationary orbit on the equatorial plane at an altitude of 36,000km above the earth's surface.
Paksat-1R will carry a communications payload to facilitate the introduction of a range of new services, including broadband internet, digital TV distribution and broadcasting, remote and rural telephony, emergency communications, tele-education and tele-medicine. The contract for Pakistan Communication Satellite (Paksat-1R) was signed between SUPARCO and China Great Wall Industry Corporation (CGWIC), on October 15, 2008, the sources said.
Work on the execution of the contract began soon after and was progressing as scheduled, the sources said, adding that the contract involved various other projects, including infrastructure and therefore it was difficult to invest an exact cost on the satellite itself. The officials said at least two new satellites - Paksat-1R and Pakistan Remote Sensing Satellite (PRSS) - would be launched in the near future.
The satellites have been developed with technical and financial assistance of China. At present, Pakistan has a communications satellite, Paksat-1, in orbit, providing coverage across Europe, Africa, the Middle East, Central Asia and the South Asian subcontinent. It is being used by TV broadcasters, telecom companies, data and broadband internet service providers and government organisations.
Paksat-1R will replace Paksat-1, a leased satellite, to ensure continuity of service. In the 1990s, Pakistan also operated a small satellite, Badr-A, in low earth orbit. However, the country's modest space programme has been oriented towards remote sensing applications. Pakistan and China have agreed to enhance strategic coordination, advance pragmatic cooperation and work together to meet challenges in pursuit of common development.
In a joint statement issued after conclusion of Chinese Prime Minister Wen Jiabao's visit to Pakistan, they declared 2011 as the "Year of China-Pakistan Friendship", and decided to hold a series of activities in the political, economic, trade, military, cultural, sporting and education fields, to warmly celebrate the 60th anniversary of the establishment of Pak-China diplomatic relations.
They decided to further implement the Framework Agreement between SUPARCO and China National Space Administration (CNSA) on Deepening Cooperation in Space Science and Technology
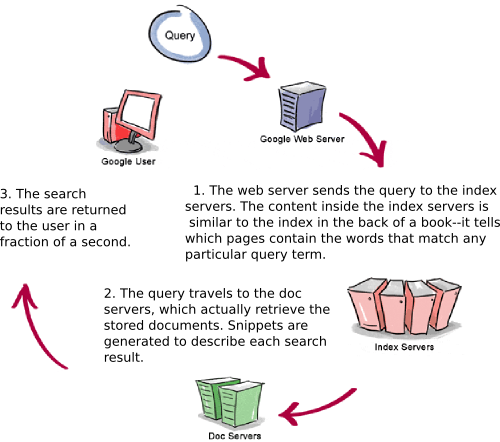
How Google Server Works????????????
1. Googlebot, Google’s Web Crawler
Googlebot is Google’s web crawling robot, which finds and retrieves pages on the web and hands them off to the Google indexer. It’s easy to imagine Googlebot as a little spider scurrying across the strands of cyberspace, but in reality Googlebot doesn’t traverse the web at all. It functions much like your web browser, by sending a request to a web server for a web page, downloading the entire page, then handing it off to Google’s indexer.Googlebot consists of many computers requesting and fetching pages much more quickly than you can with your web browser. In fact, Googlebot can request thousands of different pages simultaneously. To avoid overwhelming web servers, or crowding out requests from human users, Googlebot deliberately makes requests of each individual web server more slowly than it’s capable of doing.
Googlebot finds pages in two ways: through an add URL form, www.google.com/addurl.html, and through finding links by crawling the web.
Unfortunately, spammers figured out how to create automated bots that bombarded the add URL form with millions of URLs pointing to commercial propaganda. Google rejects those URLs submitted through its Add URL form that it suspects are trying to deceive users by employing tactics such as including hidden text or links on a page, stuffing a page with irrelevant words, cloaking (aka bait and switch), using sneaky redirects, creating doorways, domains, or sub-domains with substantially similar content, sending automated queries to Google, and linking to bad neighbors. So now the Add URL form also has a test: it displays some squiggly letters designed to fool automated “letter-guessers”; it asks you to enter the letters you see — something like an eye-chart test to stop spambots.
When Googlebot fetches a page, it culls all the links appearing on the page and adds them to a queue for subsequent crawling. Googlebot tends to encounter little spam because most web authors link only to what they believe are high-quality pages. By harvesting links from every page it encounters, Googlebot can quickly build a list of links that can cover broad reaches of the web. This technique, known as deep crawling, also allows Googlebot to probe deep within individual sites. Because of their massive scale, deep crawls can reach almost every page in the web. Because the web is vast, this can take some time, so some pages may be crawled only once a month.
Although its function is simple, Googlebot must be programmed to handle several challenges. First, since Googlebot sends out simultaneous requests for thousands of pages, the queue of “visit soon” URLs must be constantly examined and compared with URLs already in Google’s index. Duplicates in the queue must be eliminated to prevent Googlebot from fetching the same page again. Googlebot must determine how often to revisit a page. On the one hand, it’s a waste of resources to re-index an unchanged page. On the other hand, Google wants to re-index changed pages to deliver up-to-date results.
To keep the index current, Google continuously recrawls popular frequently changing web pages at a rate roughly proportional to how often the pages change. Such crawls keep an index current and are known as fresh crawls. Newspaper pages are downloaded daily, pages with stock quotes are downloaded much more frequently. Of course, fresh crawls return fewer pages than the deep crawl. The combination of the two types of crawls allows Google to both make efficient use of its resources and keep its index reasonably current.
2. Google’s Indexer
Googlebot gives the indexer the full text of the pages it finds. These pages are stored in Google’s index database. This index is sorted alphabetically by search term, with each index entry storing a list of documents in which the term appears and the location within the text where it occurs. This data structure allows rapid access to documents that contain user query terms.To improve search performance, Google ignores (doesn’t index) common words called stop words (such as the, is, on, or, of, how, why, as well as certain single digits and single letters). Stop words are so common that they do little to narrow a search, and therefore they can safely be discarded. The indexer also ignores some punctuation and multiple spaces, as well as converting all letters to lowercase, to improve Google’s performance.
3. Google’s Query Processor
The query processor has several parts, including the user interface (search box), the “engine” that evaluates queries and matches them to relevant documents, and the results formatter.PageRank is Google’s system for ranking web pages. A page with a higher PageRank is deemed more important and is more likely to be listed above a page with a lower PageRank.
Google considers over a hundred factors in computing a PageRank and determining which documents are most relevant to a query, including the popularity of the page, the position and size of the search terms within the page, and the proximity of the search terms to one another on the page. A patent application discusses other factors that Google considers when ranking a page. Visit SEOmoz.org’s report for an interpretation of the concepts and the practical applications contained in Google’s patent application.
Google also applies machine-learning techniques to improve its performance automatically by learning relationships and associations within the stored data. For example, the spelling-correcting system uses such techniques to figure out likely alternative spellings. Google closely guards the formulas it uses to calculate relevance; they’re tweaked to improve quality and performance, and to outwit the latest devious techniques used by spammers.
Indexing the full text of the web allows Google to go beyond simply matching single search terms. Google gives more priority to pages that have search terms near each other and in the same order as the query. Google can also match multi-word phrases and sentences. Since Google indexes HTML code in addition to the text on the page, users can restrict searches on the basis of where query words appear, e.g., in the title, in the URL, in the body, and in links to the page, options offered by Google’s Advanced Search Form and Using Search Operators (Advanced Operators).
Let’s see how Google processes a query.
Window 7 Laptop And Wi-fi
One of the wireless sharing tools that Windows 7 was supposed to have was the ability to turn any computer running Windows 7 into a WiFi hotspot. Unfortunately, Microsoft didn’t include that feature in the final release of Windows 7.
Thanks to a program called Connectify, you can get that feature back and turn your Windows 7-powered laptop into a WiFi hotspot so you can share your Internet connection with family, friends, classmates, co-workers and other mobile devices.
Connectify is a free and easy to use software router for Windows 7 computers. With Connectify, users can wireless share any Internet connection: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Connectify hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.
Popular Use Cases:
1. Home – You can use Connectify to act as a repeater for your home router and extend its range. You can also use it to share your WiFi connection to friends and visitors without having to provide the real SSID and password, keeping your network more secure.
2. School – Many schools and educational institutions limit the number of devices that a person can register to the wireless networks. By using Connectify, you bypass these limitations and securely connect other mobile devices to your personal WiFi network.
3. On the Road – For people who are always on the go and travel a lot, having a reliable Internet connection is very important. Not all airports, hotels, coffee shops and restaurants offer free WiFi and could charge around $10-15 per connection. With Connectify, you can share both the expense and the Internet connection with family, friends or co-workers. Most hotels offer free Internet connection, however they only provide access via an ethernet cable meaning you can’t access for your WiFi only mobile devices.
One of the wireless sharing tools that Windows 7 was supposed to have was the ability to turn any computer running Windows 7 into a WiFi hotspot. Unfortunately, Microsoft didn’t include that feature in the final release of Windows 7.
Thanks to a program called Connectify, you can get that feature back and turn your Windows 7-powered laptop into a WiFi hotspot so you can share your Internet connection with family, friends, classmates, co-workers and other mobile devices.
Connectify is a free and easy to use software router for Windows 7 computers. With Connectify, users can wireless share any Internet connection: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Connectify hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.
Popular Use Cases:
1. Home – You can use Connectify to act as a repeater for your home router and extend its range. You can also use it to share your WiFi connection to friends and visitors without having to provide the real SSID and password, keeping your network more secure.
2. School – Many schools and educational institutions limit the number of devices that a person can register to the wireless networks. By using Connectify, you bypass these limitations and securely connect other mobile devices to your personal WiFi network.
3. On the Road – For people who are always on the go and travel a lot, having a reliable Internet connection is very important. Not all airports, hotels, coffee shops and restaurants offer free WiFi and could charge around $10-15 per connection. With Connectify, you can share both the expense and the Internet connection with family, friends or co-workers. Most hotels offer free Internet connection, however they only provide access via an ethernet cable meaning you can’t access for your WiFi only mobile devices.
Connectify is 100% free and unrestricted, compatible with
any WiFi enabled device and most importantly, it is reliable
and secure. It is available to download for FREE only for
computers running Windows 7.
Best Inventions of 2008
Here’s the complete list of the 50 Best Inventions of 2008 in descending order.
50. A Camera For the Blind
49. Sound-Enhanced Food
48. The Time Eater Clock
47. Google’s Floating Data Center
46. Aptera Electric Car
45. The Short Refinance
44. Sunscreen for Plants
43. High-Tech Running Shoes
42. Disemvoweling
41. The Peraves MonoTracer
40. The Seven New Deadly Sins
39. Enhanced Fingerprints
38. The Baseball Instant Replay
37. Smog-Eating Cement
36. The New Ping-Pong Serve
35. Airborne Wind Power
34. Made-in-Transit Packaging
33. Biomechanical Energy Harvester
32. Facebook for Spies
31. Einstein’s Fridge
30. The Internet Of Things
29. The 46th Mersenne Prime
28. The Invisibility Cloak
27. Bubble Photography
26. The Speedo LZR Racer
25. Thin-Film Solar Panels
24. Bionic Contacts
23. The Branded Candidate
22. The Shadowless Skyscraper
21. The Synthetic Organism
20. The Everything Game
19. Montreal’s Public Bike System
18. The New Mars Rover
17. The Mobile, Dexterous, Social Robot
16. The Dynamic Tower
15. The Direct-to-Web Supervillain Musical
14. The Bionic Hand
13. The Memristor
12. Housing Funds
11. Green Crude
10. The World’s Fastest Computer
9. The Orbital Internet
8. Bullets That Shoot Bullets
7. The Chevy Volt
6. The Global Seed Vault
5. The Large Hadron Collider
4. Hulu.com
3. The Lunar Reconnaissance Orbiter
2. The Tesla Roadster
1. The Retail DNA Test























